Is there a more secure way to store my information than using an ID and password?
Secure Sockets Layer (SSL) is used to encrypt the route to InfiniCLOUD. The encrypted layout is used to connect IDs and passwords to the server.
A defined strength exists since the password database on the server is encrypted by a one-way function (hashed) owned by the Operating System (OS).
There are numerous instances when user IDs are swapped by individuals who use public features, or where they are made to match those of a Social Networking Site (SNS) such as Twitter, Facebook, or Instagram.
As a result, there are times when it is thought that protecting saved data is insufficient because the security of the password is fully dependent on the strength of the password.
In general, there are three different approaches to encrypt data.
*The only method that can be used with InfiniCLOUD is Method 3.
(1) How to send the user's password to the server and encrypt the key held on the server using it
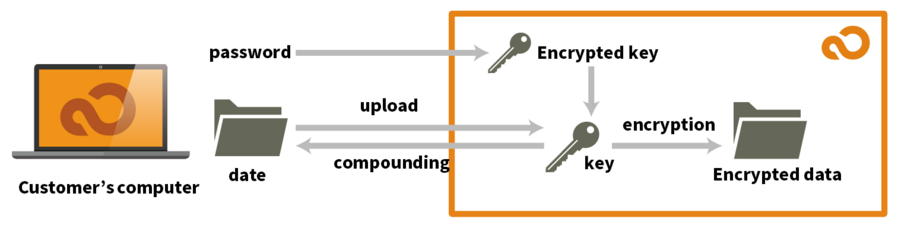
The key for data encryption and decryption is stored on the server in this technique.
Passwords are updated on a regular basis at the user's discretion. Because passwords have a low strength, it is important to update the randomly generated key that encrypted and decrypts data and the server rather than encrypting the data to the password itself. When the user updates heir password, encrypted data decrypts the key stored on the server-side with the password supplied from the client, and then decrypts the data using that key. Furthermore, there is no need to re-encrypt data on the server. This approach, however, does possess the following drawbacks.
- Because of its ability to decode the key with a password made up of many alphanumeric letters and symbols entered by the user, it cannot claim sufficient strength.
- The decryption key is stored on the server, despite the fact that the user encrypted their account with their password.
- It is impossible to manage with a situation in which a user's password is disclosed. The most serious of these incidents is password leakage.
There is no change in the state using this strategy, which relied solely on the strength of the password given by the consumer. The data will be decrypted if the encrypted key and data leak. It is in the best interest of the user to be aware of the following: As the "shared function" is incompatible based on specific criteria, many users shared data on InfiniCLOUD is compounded during the creation of a shared folder not consisting of a password.
*InfiniCLOUD process each file individually to avoid data damage. The user may be unable to access the service due to the lengthy encryption/decryption process.
(2) How to send a key file every time
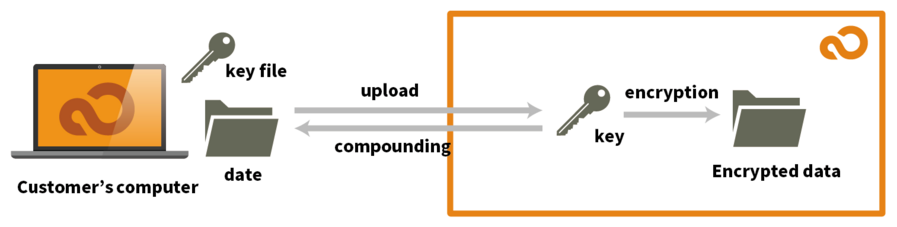
Method 2 differs from the previous method in that it delivers a client-generated key to the server. The route is SSL-encrypted, as previously stated. The transmission of the key will become more reliable. Standard client software cannot be used since the server uses a proprietary protocol. Only the use of a web browser will be permitted.
InfiniCLOUD highlights that ordinary client software can be utilized with it. It will, however, become incompatible with InfiniCLOUD's service due to its size.
(3) Having an encryption engine and sending encrypted data as is
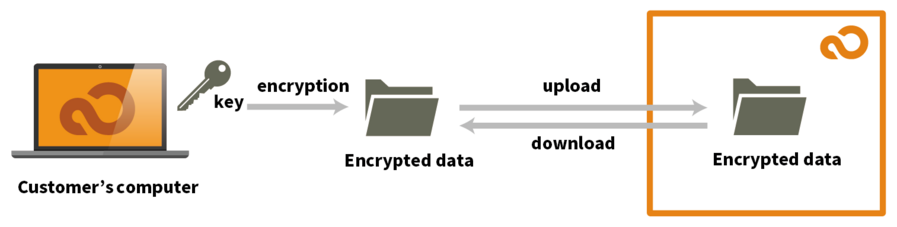
In addition to method 2, only encrypted data is saved on the server for clients processing their encryption engine using this approach.
The advantage of this method is that if data is mistakenly leaked, compounding the data is almost hard, even if the data is encrypted.
It is impossible to tell what kind of files are contained within data that is encrypted volume by volume rather than file unit by file unit.
Files that the user desires to share can be uploaded independently from the aforementioned information, making the process more convenient and secure.
Data that is encrypted volume by volume instead of by file unit makes it difficult to know what kind of files are contained within the data. Files that the user desires to share can be uploaded independently from the aforementioned information, making the process more convenient and secure.
InfiniCLOUD can only perform method 3 as of June 2019.
There are various encrypting methods from the perspective of the customer's computer. VeraCrypt and the encrypted "Sparse Bundle/Disk Image" of Mac OS X are popular choices. If VeraCrypt is the customer's preferred encryption method, InfiniCLOUD recommends starting with volume of about 1GB. This is due to the transfer of massive amounts of data on a regular basis.
Updated January 28, 2016